CVE-2021-1675(Windows Print Spooler 远程命令执行漏洞)漏洞通告 | PoC公开
-
作者:火绒安全
-
发布时间:2021-06-30
-
阅读量:3111
本月微软官方发布安全补丁更新,修复了一处存在于 Windows Print Spooler的远程命令执行漏洞,CVE编号为CVE-2021-1675,攻击者可以绕过安全检查并写入恶意驱动程序。6月29日,该漏洞PoC被公开,火绒已在6月9日/10日对个人版/企业版进行了补丁推送。鉴于该漏洞有被利用的可能,我们建议用户尽快使用火绒漏洞修复功能更新补丁。
(注:6月已进行过漏洞修复的用户无需再次修复)
一、漏洞详情
Windows Print Spooler 远程代码执行漏洞 CVE-2021-1675
严重级别:高危 CVSS:7.8
被利用级别:有可能被利用
Print Spooler 是 Windows打印后台处理服务,在Windows平台使用打印机的必要服务。攻击者可绕过 RpcAddPrinterDriver 的身份验证,在打印服务器中安装恶意驱动程序。Windows域环境中普通帐户就能利用此漏洞。
二、影响范围
- Windows 10 Version 1809 for 32-bit Systems
-
- Windows Server 2012 R2 (Server Core installation)
-
- Windows Server 2012 R2
-
- Windows Server 2012 (Server Core installation)
-
- Windows Server 2012
-
- Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
-
- Windows Server 2008 R2 for x64-based Systems Service Pack 1
-
- Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
-
- Windows Server 2008 for x64-based Systems Service Pack 2
-
- Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
-
- Windows Server 2008 for 32-bit Systems Service Pack 2
-
- Windows RT 8.1
-
- Windows 8.1 for x64-based systems
-
- Windows 8.1 for 32-bit systems
-
- Windows 7 for x64-based Systems Service Pack 1
-
- Windows 7 for 32-bit Systems Service Pack 1
-
- Windows Server 2016 (Server Core installation)
-
- Windows Server 2016
-
- Windows 10 Version 1607 for x64-based Systems
-
- Windows 10 Version 1607 for 32-bit Systems
-
- Windows 10 for x64-based Systems
-
- Windows 10 for 32-bit Systems
-
- Windows Server, version 20H2 (Server Core Installation)
-
- Windows 10 Version 20H2 for ARM64-based Systems
-
- Windows 10 Version 20H2 for 32-bit Systems
-
- Windows 10 Version 20H2 for x64-based Systems
-
- Windows Server, version 2004 (Server Core installation)
-
- Windows 10 Version 2004 for x64-based Systems
-
- Windows 10 Version 2004 for ARM64-based Systems
-
- Windows 10 Version 2004 for 32-bit Systems
-
- Windows 10 Version 21H1 for 32-bit Systems
-
- Windows 10 Version 21H1 for ARM64-based Systems
-
- Windows 10 Version 21H1 for x64-based Systems
-
- Windows 10 Version 1909 for ARM64-based Systems
-
- Windows 10 Version 1909 for x64-based Systems
-
- Windows 10 Version 1909 for 32-bit Systems
-
- Windows Server 2019 (Server Core installation)
-
- Windows Server 2019
-
- Windows 10 Version 1809 for ARM64-based Systems
-
- Windows 10 Version 1809 for x64-based Systems
三、修复建议
1、通过火绒个人版/企业版【漏洞修复】功能修复漏洞。
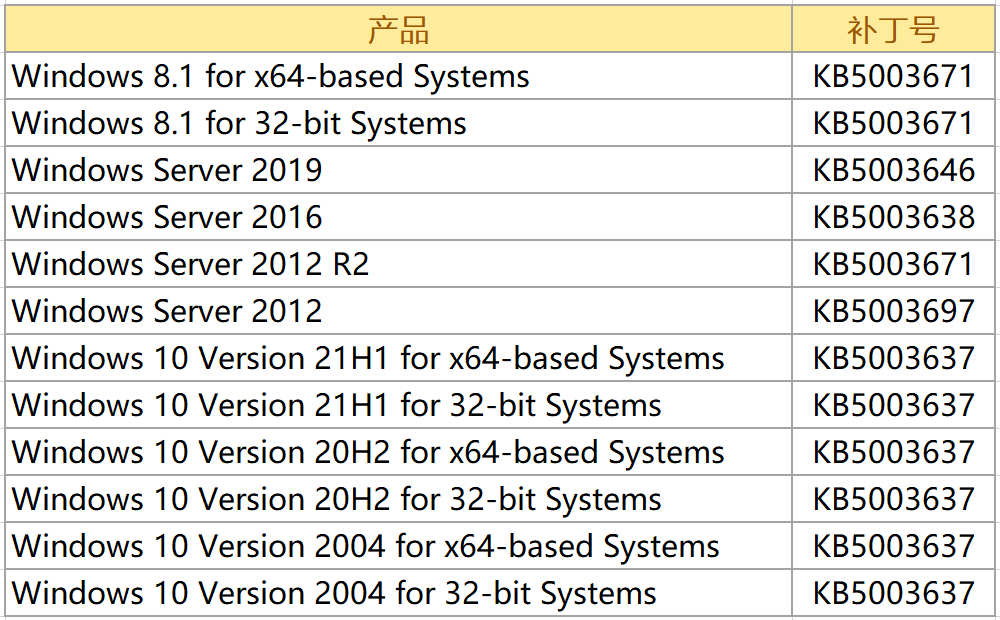
2、下载微软官方提供的补丁
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2021-1675
参考链接:
https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-1675












